2. Cryptographic Tools
2-1. Confidentiality with Symmetric Encryption
- Symmetric(= Conventional, Single-key) Encryption
Used for secret communication in various fields
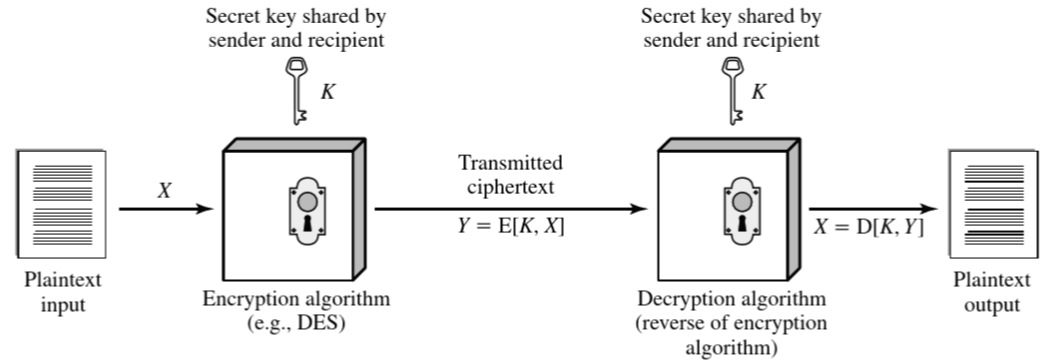
| Plaintext | input to encryption algorithm, the original message or data |
| Secret key | input to encryption algorithm, the exact substitutions and transformations depend on the key |
| Encryption Algorithm | performing various substitutions and transformations on the plaintext |
| Ciphertext | scrambled message produced as output |
| Decryption Algorithm | taking the ciphertext and the secret key and produces the original plaintext |
There are two requirements:
1. The opponent should be unable to decrypt ciphertext or discover the key → need a strong encryption algorithm
2. The sender and receiver must have copies of secret key in a secure fashion and keep them secure
There are two general approaches to attacking a symmetric encryption scheme:
1. cryptanalysis: to attempt to deduce a specific plaintext or the key being used
2. brute-force attack: to try every possible key on a piece of ciphertext
- Symmetric Block Encryption Algorithm
Block cipher: to process the plaintext input in fixe-size blocks and produces a block of ciphertext of equal size for each plaintext block(DES, triple DES, AES...)
| DES (Data Encryption Standard) |
56-bit key length makes it vulnerable to a brute-force attack |
| Triple DES | to repeat DES 3 times using either 2 or 3 unique keys with its 168-bit key length, it overcomes the vulnerability to brute-force attack of DES relatively sluggishing and small block size(64-bit) |
| AES (Advanced Encryption Standard) |
128-bit block size and 256-bit key size -> improving efficiency and security strength |
ECB(Electronic Codebook) mode:
▷ Each block of plaintext is encrypted using the same key
▷ For lengthy data, it may not be secure because of being exploited regularities to ease the task of decryption → "modes of operation" overcome this
- Stream Ciphers
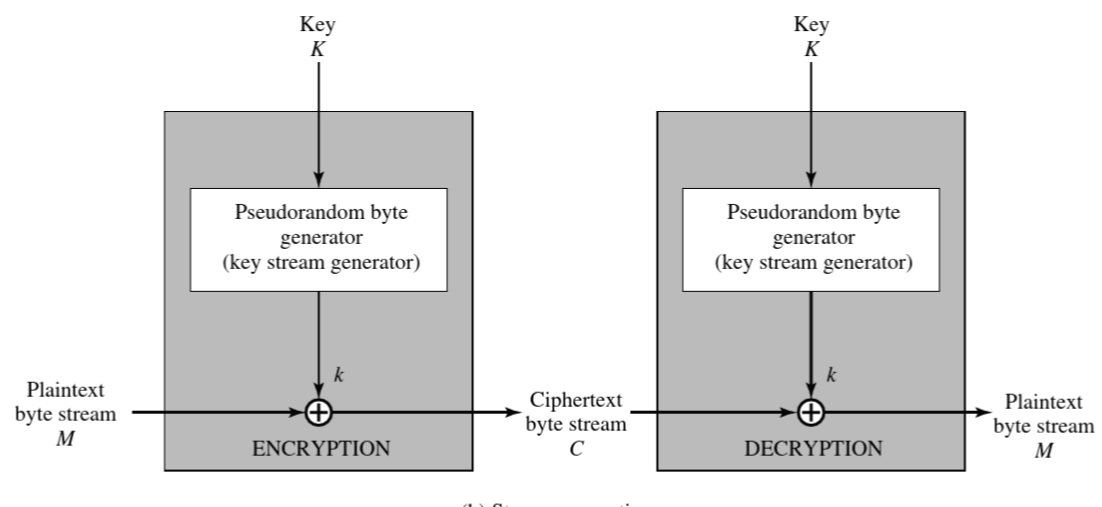
▷ Keystream(the output of the generator) is combined one byte at a time with the plaintext stream using the bitwise XOR operation
▷ Stream ciphers are always faster and use far less code than do block ciphers(but block ciphers can reuse the key)
2-2. Message Authentication and Hash Functions
- Message Authentication and Encryption
Message authentication: for data integrity, process to verify that received or stored messages are authentic
Symmetric encryption alone is not a suitable tool for data authentication(reordering is a threat)
→ It is possible to combine encrypted messages and authentication tag
Message Authentication Code:
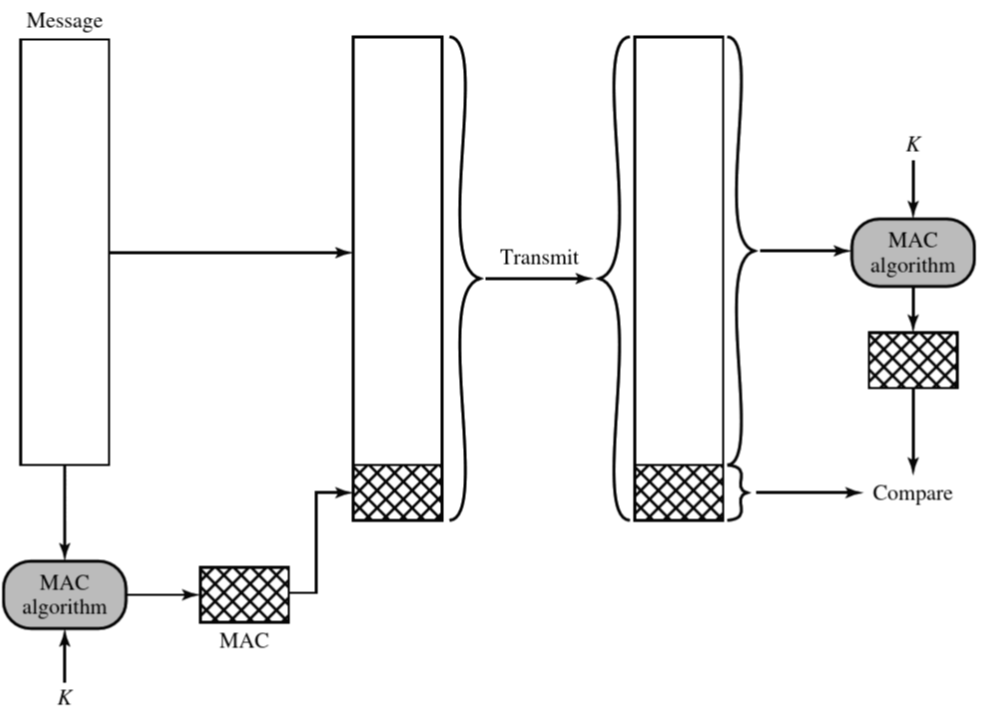
▷ Assuming that A and B share a secret key $K_{AB}$, and both calculate the message authentication code as a complex function -> $MAC_{m} = F(K_{AB}, M)$
▷ Authentication algorithm is similar to encryption, but one difference is that it need not be reversible
One-way Hash Function:
Amazon.com
Enter the characters you see below Sorry, we just need to make sure you're not a robot. For best results, please make sure your browser is accepting cookies.
www.amazon.com
2. Cryptographic Tools
2-1. Confidentiality with Symmetric Encryption
- Symmetric(= Conventional, Single-key) Encryption
Used for secret communication in various fields

| Plaintext | input to encryption algorithm, the original message or data |
| Secret key | input to encryption algorithm, the exact substitutions and transformations depend on the key |
| Encryption Algorithm | performing various substitutions and transformations on the plaintext |
| Ciphertext | scrambled message produced as output |
| Decryption Algorithm | taking the ciphertext and the secret key and produces the original plaintext |
There are two requirements:
1. The opponent should be unable to decrypt ciphertext or discover the key → need a strong encryption algorithm
2. The sender and receiver must have copies of secret key in a secure fashion and keep them secure
There are two general approaches to attacking a symmetric encryption scheme:
1. cryptanalysis: to attempt to deduce a specific plaintext or the key being used
2. brute-force attack: to try every possible key on a piece of ciphertext
- Symmetric Block Encryption Algorithm
Block cipher: to process the plaintext input in fixe-size blocks and produces a block of ciphertext of equal size for each plaintext block(DES, triple DES, AES...)
| DES (Data Encryption Standard) |
56-bit key length makes it vulnerable to a brute-force attack |
| Triple DES | to repeat DES 3 times using either 2 or 3 unique keys with its 168-bit key length, it overcomes the vulnerability to brute-force attack of DES relatively sluggishing and small block size(64-bit) |
| AES (Advanced Encryption Standard) |
128-bit block size and 256-bit key size -> improving efficiency and security strength |
ECB(Electronic Codebook) mode:
▷ Each block of plaintext is encrypted using the same key
▷ For lengthy data, it may not be secure because of being exploited regularities to ease the task of decryption → "modes of operation" overcome this
- Stream Ciphers

▷ Keystream(the output of the generator) is combined one byte at a time with the plaintext stream using the bitwise XOR operation
▷ Stream ciphers are always faster and use far less code than do block ciphers(but block ciphers can reuse the key)
2-2. Message Authentication and Hash Functions
- Message Authentication and Encryption
Message authentication: for data integrity, process to verify that received or stored messages are authentic
Symmetric encryption alone is not a suitable tool for data authentication(reordering is a threat)
→ It is possible to combine encrypted messages and authentication tag
Message Authentication Code:

▷ Assuming that A and B share a secret key $K_{AB}$, and both calculate the message authentication code as a complex function -> $MAC_{m} = F(K_{AB}, M)$
▷ Authentication algorithm is similar to encryption, but one difference is that it need not be reversible
One-way Hash Function:
Amazon.com
Enter the characters you see below Sorry, we just need to make sure you're not a robot. For best results, please make sure your browser is accepting cookies.
www.amazon.com
